
POPSEC is a series drawing on popular media to convey important security lessons—how to emulate best practices, analyze mistakes, and strive not to repeat errors. Mad Max: Fury Road is full of both good and bad examples of security practices. While the following contains all kinds of spoilers, it’s also full of life lessons we can draw from scrutinizing the successes and mishaps on the Fury Road.
Lesson 1: If You Liked It then You Should Have Put a Lock On It
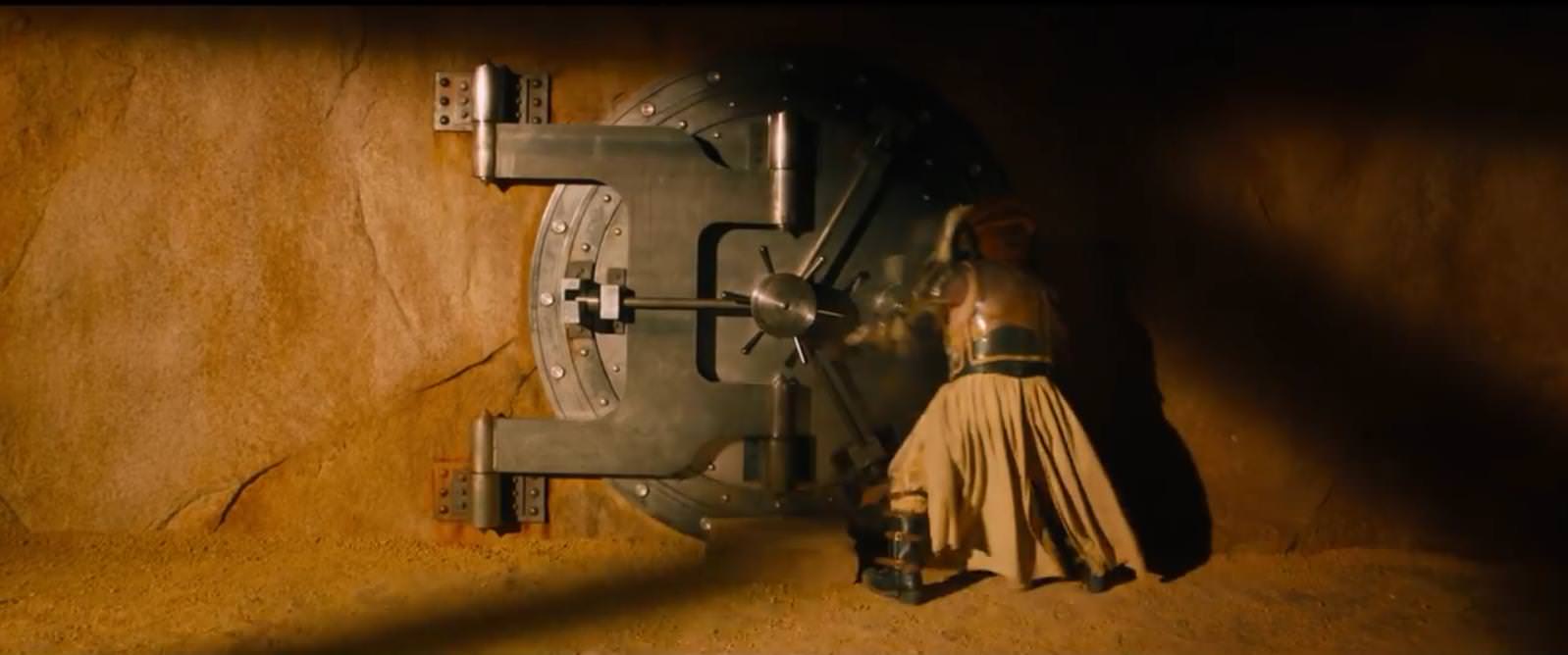
Now, of course it’s wrong to keep women locked in a vault like property, but there’s an important lesson to be learned from Immortan Joe’s objectification of women and subsequent failure to “keep them in their place”: if you care about something, secure it. If it’s important to you that something not make it out into the world, be it a physical object or information, lock it up using a robust passphrase (or sturdy physical lock). Keeping your prized possessions in a vault is no good if the vault isn’t secured with a sufficiently complex combination.
Lesson 2: Assess Your Adversaries

This seems like a pretty obvious statement, but it’s actually an important operational security lesson: you don’t want to be a porcupine trying to take down a war rig. When assessing your threats, it’s important to make sure you’re not biting off more than you can chew. While it’s true that we don’t always have a choice in adversaries, it’s also wise to avoid initiating confrontations if you’re not at least reasonably sure you can come out on top. On the Fury Road, this might look like not trying to take on a juggernaut being driven by Imperator Furiosa, but in the real world this might look like peacing out from a dicey action if you didn’t roll in with your affinity group, or staying away from the barricades if you’ve been personally targeted for arrest in the past. The State has nearly unlimited resources for repression, and it is very important to learn how to be strategic in your opposition.
Lesson 3: Prepare for the Worst

Whether you’re driving into a dust storm or running through clouds of tear gas1, it’s important to anticipate the possibility of these circumstances ahead of time, and plan accordingly with regard to things like personal protective equipment, tactics, and exit strategies. This is obviously true on the Fury Road, but is also worthwhile in the context of demonstrations and direct action. Familiarize yourself with the repression tactics (and environmental circumstances) you are likely to face and plan accordingly. Keep in mind that “planning accordingly” may look different depending on whether your intention is to stick around or to make a purposeful and orderly getaway. If you intend to remain on the scene when tear gas is deployed, you may wish to invest in a respirator or gas mask. If you intend to leave in the event that chemical weapons are deployed, a damp bandanna may be sufficient for your needs. This level of preparation requires a great deal of forethought and research, but it is well worth the effort.
Lesson 4: Use Robust Passphrases

The corollary to Lesson 1 is—when you do use a passphrase (or lock) to secure something you care about, make sure it’s a robust one. Furiosa uses a sequence of switch flips and button pushes2 to achieve sufficient complexity, but in the real world you might consider either using passphrases constructed from a series of unrelated words, random passphrases generated by a password manager, or a combination of both. There are varying schools of thought regarding biometric locks (fingerprints, retinal scans, etc.), but they do work well for a select set of threat profiles, and are worth looking into as an option.
Lesson 5: Barriers Will Not Stop Determined Adversaries, and That’s OK!

Furiosa’s deal with the Rock Riders involves causing a landslide to block off their canyon once she’s through, in order to stop her pursuers in their tracks. A few of her foes are buried under the rubble, and some can’t get over it, but with enough time and effort Immortan Joe is eventually able to drive over it with much of his cohort. Similar scenarios exist in real-life security culture. When discussing security and security precautions, the discourse takes on a somewhat nihilistic tone due to the fact that with enough time and resources, any security can be broken. Yet in most cases, it is actually not necessary to have “perfect” security. Usually, the adversaries we are facing have neither the will nor the limitless resources to circumvent the roadblocks we place in their way. Additionally, the goal in security doesn’t really need to be stopping adversaries in their tracks, but rather delaying them long enough to accomplish our aims.
On the Fury Road, the time Immortan Joe spent overcoming the obstacle of the roadblock gave Furiosa and her crew a significant amount of time and space to maneuver. In our own security practices, this translates to the idea that using encryption is always better than not. Encryption should never be treated as a magic shield. Encryption doesn’t necessarily keep your messages from being read by people other than the intended recipient, but it can make intercepting your communications difficult enough, time-consuming enough, and resource-intensive enough that most adversaries will decide it’s not worth the trouble and move on.
Lesson 6: Try Not to Create a Single Point of Failure

When creating a security strategy for yourself, make sure it never relies solely on one tool or tactic. Immortan Joe diverted all of his resources, as well as the resources from neighboring Gas Town and the Bullet Farm, in order to pursue and overtake Furiosa. When he failed to catch her, this left the Citadel defenseless against her return. Likewise, your plan to stay safe and secure will fail if you rely only on any one tool, tactic, or individual. What does this mean in terms of practical application? It means you should be looking to build “defense in depth.” That is to say, you should be choosing tools and strategies which help protect you, and also communicating in ways which are not inherently incriminating if any of those tools cease to be secure, or strategies fail to be effective. Tools and tactics should be varied and disposable, and the loss or compromise of one should never be sufficient to land you and your comrades in prison. Secure communication tools are important supplements to strong operational security practices and good judgement.
Lesson 7: Be Selective about the Information You Offer

I’m real happy for you, and I’mma let this piece finish, but Max Rockatansky had the best security culture of all time. Dude managed to insinuate himself into a group of suspicious women, gain their trust, and ingratiate himself to the point of being able to talk them into GOING BACK THE SAME WAY THEY CAME, all without ever even giving his name, never mind any other personal details. Now, Max is a pretty cool guy, and is actually honorable and trustworthy, and his operational security is absolutely something we all should strive to emulate… HOWEVER, there is an important consideration to keep in mind: despite the fact that Max offered little to no personal information to his comrades, Furiosa and friends still had a pretty good idea of what his motives were, what he stood to gain from assisting them, and that he would not benefit from betraying them.
Play your cards close to your vest, try to understand that others will do the same, and don’t place your trust in someone whose motives are unclear. You don’t need to know someone’s life story, but it’s worthwhile to know what they stand to gain from helping you, and what they gain from screwing you over.
— By Elle Armageddon


